Performing an Expanded Data Breach Risk Scan
- After logging onto the Risk Intelligence Console, click on Scan Computers in the side navigation panel.
- To change the organization you want to scan, click on Change and select the appropriate organization from those available.
- From the Choose a Scan Type list select Expanded Data Breach Risk Scan.
- From the Scan Delivery Method dropdown select Command Line Executable.
- Once you have chosen your command line scan option, enter the appropriate script to run the scan.
In the Choose Organization section, the currently selected organization is shown.
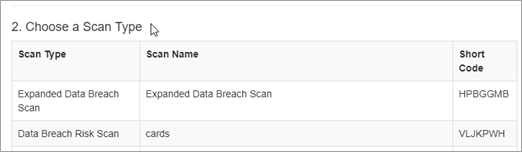
Short codes can be used as command line arguments to the CLI scanner as described in the next step.
The various platforms and corresponding deployment options for the CLI scanner are displayed.
As the scan runs, you can monitor its progress and view the scan results of individual devices from the View and Manage - Scan Results page - see Monitoring Scan Progress and Viewing Individual Device Scan Results.
Once one or more scans have completed you will be able to report on results in the Reporting module. See Reporting and in particular Generating an Expanded Data Breach Risk Report.
